
IT Asset Recovery

Protect your business and Stay Compliant
Protect your company’s assets and ensure compliance with our Secure Data Destruction services. Foolproof solutions to eliminate sensitive data on end-of-life IT assets. Don’t risk data leaks – choose security and peace of mind.
Request a quoteIn today’s digital age, data is as valuable as currency. And disposing of it securely is non-negotiable.
Our Certified Data Destruction services go beyond ticking compliance boxes like GDPR; they’re about safeguarding your company’s reputation and intellectual property.
Seamlessly integrate trusted data destruction into your lifecycle management strategy, fortifying your enterprise against potential vulnerabilities.
Contact us todayIn today’s connected world, protecting sensitive data isn’t optional, it’s essential. While active data security gets most of the attention, end‑of‑life data is often forgotten, creating unnecessary risk.
Data destruction should be a core part of your IT lifecycle strategy because it ensures:

Using Blancco’s certified data erasure software, we securely wipe your data storage devices either on-site or off-site, depending on your preference and regulatory requirements. Rest easy knowing your confidential business data is permanently deleted. You’ll receive a data removal certificate, while the device remains functional and retains its value.
Using high-power shredders, we offer a fail-safe method to irreversibly destroy information from hard drives and other data storage media. This service can be conducted on-site or off-site as per your needs and regulations. Devices are physically rendered unusable, and you’ll receive a certificate of destruction.
Our services comply with standards such as WEEELABEX, DIN 66399, E5 and H5, NIST 800-88, ISO 27001 and NEN 7510.
IT Asset Disposition
We help you dispose of, recycle, reuse or sell your IT equipment at the end of its lifecycle – securely and responsibly.
Request a valuation
While many companies have on-site or off-site data destruction built into their security policies, you’re often still left with surplus or outdated IT that doesn’t actually need to be destroyed.
What if you could recycle these devices instead?
Receive tax advantages, strengthen your CSRD results, and advance digital equality through donation.
Ask about hardware donation
From corporate IT to community impact with Mace Construct
Mace Construct is a global delivery consultancy and construction company headquartered in London. Circular IT group has supported Mace globally for 10+ years, delivering ITAD and lifecycle management services as a trusted strategic partner. This long-term collaboration enables Mace to securely manage retired IT assets while achieving their carbon reduction and sustainability targets.

From Secure IT Asset Disposal to Community Impact with firmus energy
Discover how Firmus Energy Supply managed secure, compliant IT asset disposal while turning retired IT into meaningful community impact.

How Assuralia helped Digital for Youth donate their 28,000th laptop to charity
How a laptop donation programme helped deliver 28,000 laptops to charity, supporting digital inclusion while reducing e-waste.
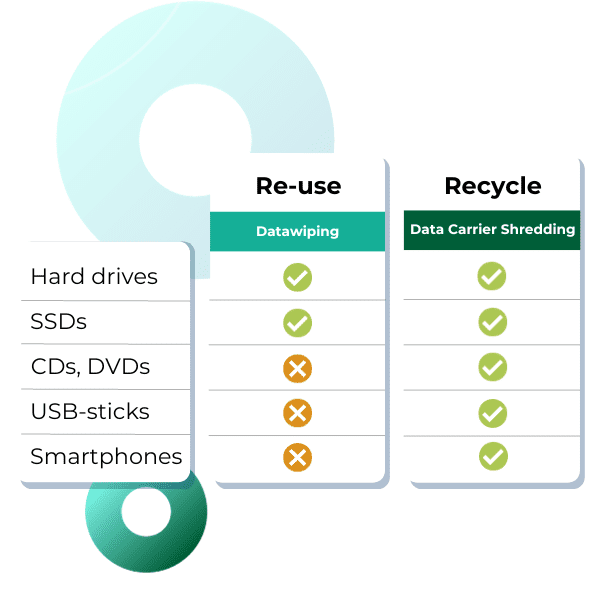
Data wiping involves erasing data from the data carrier by means of software. This is the most circular option because the data carrier is reusable after this. Since the data is not recoverable, you can reuse or sell the data carrier itself.
In data destruction, a data carrier is physically destroyed by the shredder. As a result, the data cannot be recovered, but the data carrier is also no longer usable.
We understand that the data on your IT equipment is crucial, and you want to be certain that it’s securely wiped when you sell it to us. That’s why we follow a strict process to ensure that all your data is permanently deleted before we proceed with the equipment.
Every piece of equipment is carefully logged first, giving you continuous insight into the status of your IT equipment’s processing. You’ll receive clear reports and the necessary deletion certificates at the end.
Here’s how it works:
Please note: This will, of course, negatively impact the residual value of your equipment.
Compliance with legislation: Our data wiping process complies with relevant laws and regulations, such as the GDPR in Europe, ensuring that your privacy and security are fully protected.
We collect the hardware using our own transport, and our service centres, where the equipment is stored, are heavily secured. This entire process ensures that you can sell your IT equipment to us with peace of mind, knowing that your data is in safe hands and will never fall into the wrong hands.
Yes, in theory, you can destroy data yourself. But the big question is: are you doing it properly? Many companies think that simply formatting a hard drive or physically damaging a data carrier is sufficient.
Unfortunately, that is a dangerous misconception. Smart hackers and data experts can still retrieve sensitive business information, even from drives that appear to be completely unusable.
At Circular IT group, we not only destroy regular and external hard drives, but also a wide range of other used data carriers. These include SSDs, tapes, smartphones, PDAs and other mobile devices.
You can also come to us for the secure destruction of USB sticks, SD cards, magnetic tapes, ID cards and more.
Curious about all the possibilities within our IT Asset Disposition (ITAD) services? View our options here.

Daan van Nieuwenhoven
Fill in the form below form and we will respond to you promptly.
"*" indicates required fields